SHA256 Hash Generator
SHA256 Hash Function Generator and Calculator is online tool to convert text to SHA256 hash Online. SHA256 Calculator Secure and one of the best tool. Generate the SHA256 hash of any string. SHA-256 produces a 256-bit (32-byte) hash value.
If you use this great tool then please comment and/or like this page.
Average Rating: Tool Views: 637
Average Rating: Tool Views: 637
Subscribe for Latest Tools
How to use this SHA256 Hash Generator Tool?
How to use Yttags's SHA256 Hash Generator?
- Step 1: Select the Tool

- Step 2: Enter The Text And Click On Generate SHA-256 Hash Button
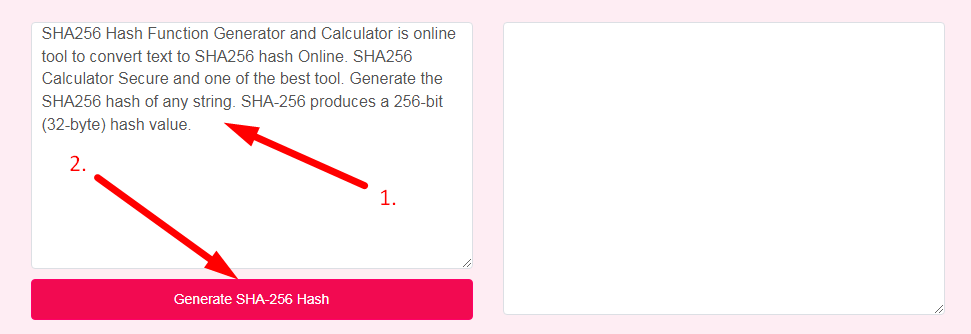
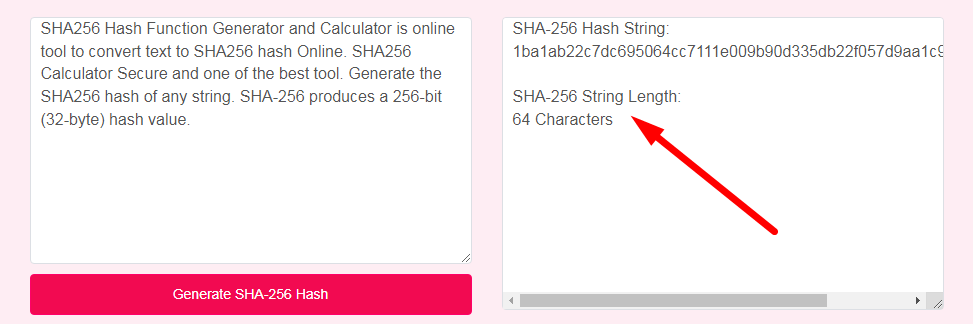
- Step 3: Check Your SHA256 Hash Generator Result
If you want to link to Sha256 Hash Generator page, please use the codes provided below!
FAQs for SHA256 Hash Generator
What is a SHA256 Hash Generator?
A SHA256 Hash Generator is a tool that computes the SHA-256 cryptographic hash function on input data, producing a fixed-size and unique hash value. This is often used for data integrity verification and secure storage of sensitive information.
What is the maximum length of SHA256 hash?
The hash size for the SHA256 algorithm is 256 bits.
What is the purpose of SHA 256 hash?
SHA-256 can help secure SSL/TLS (Transport Layer Security) certificates by creating a digital signature your device can verify. For example, when a server presents its TLS certificate to clients such as web browsers, the client can then use the corresponding public key to decrypt and verify the signature.
How the hash is generated using SHA256?
Generating an SHA-256 hash involves running the input data through a complex mathematical function that produces a unique output value. This output value is the hash, which serves as a digital fingerprint of the input data.
What is the input size of SHA?
The secure hash algorithm with a digest size of 256 bits, or the SHA 256 algorithm, is one of the most widely used hash algorithms.